Unverified and Suspicious Tokens in Gem Wallet
When using Gem Wallet, you may notice tokens in your wallet marked with badges indicating their status:
Understanding these labels is crucial for safely managing your cryptocurrency and avoiding potential scams. This FAQ explains the differences, how Gem Wallet identifies these tokens, and best practices for handling them.
Why Do These Tokens Appear in My Wallet?
Gem Wallet displays all tokens associated with your wallet’s address on supported blockchains. Since blockchain addresses are public, anyone can send tokens to your wallet, including unverified or suspicious ones. These often come from:
- Airdrops: Unsolicited tokens sent to promote a project or lure users into scams.
- Manual Imports: Tokens you’ve added using a contract address.
- Transactions: Tokens received from other wallets or unknown exchanges.
- Scams: Tokens sent as part of fraudulent schemes, such as investment or phishing sites, designed to trick users into engaging with suspicious platforms or contracts.
Just because a token appears in your wallet doesn’t mean it’s safe to interact with. Gem Wallet allows you to easily add a token, but it is your responsibility to always verify its legitimacy.
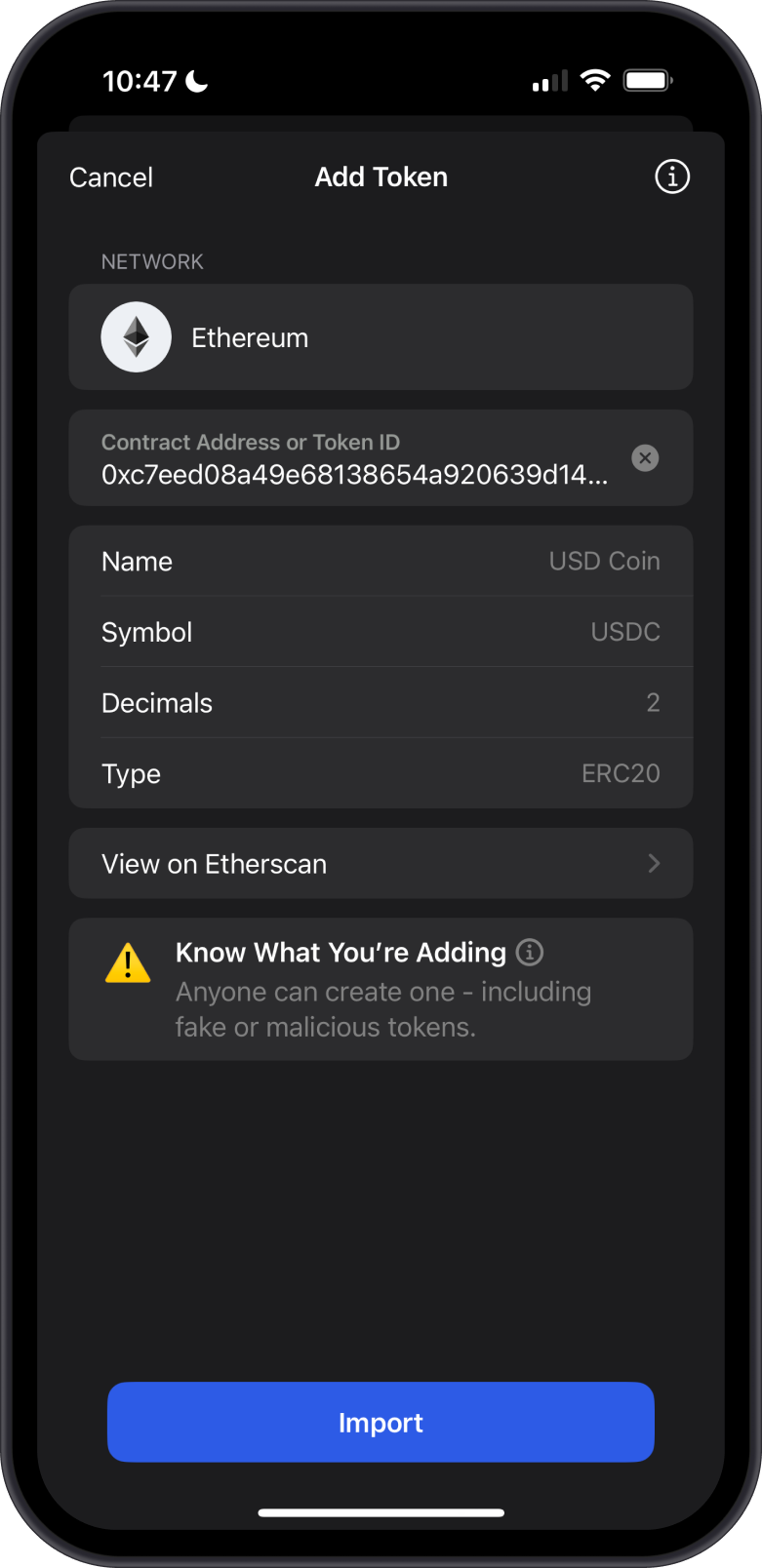
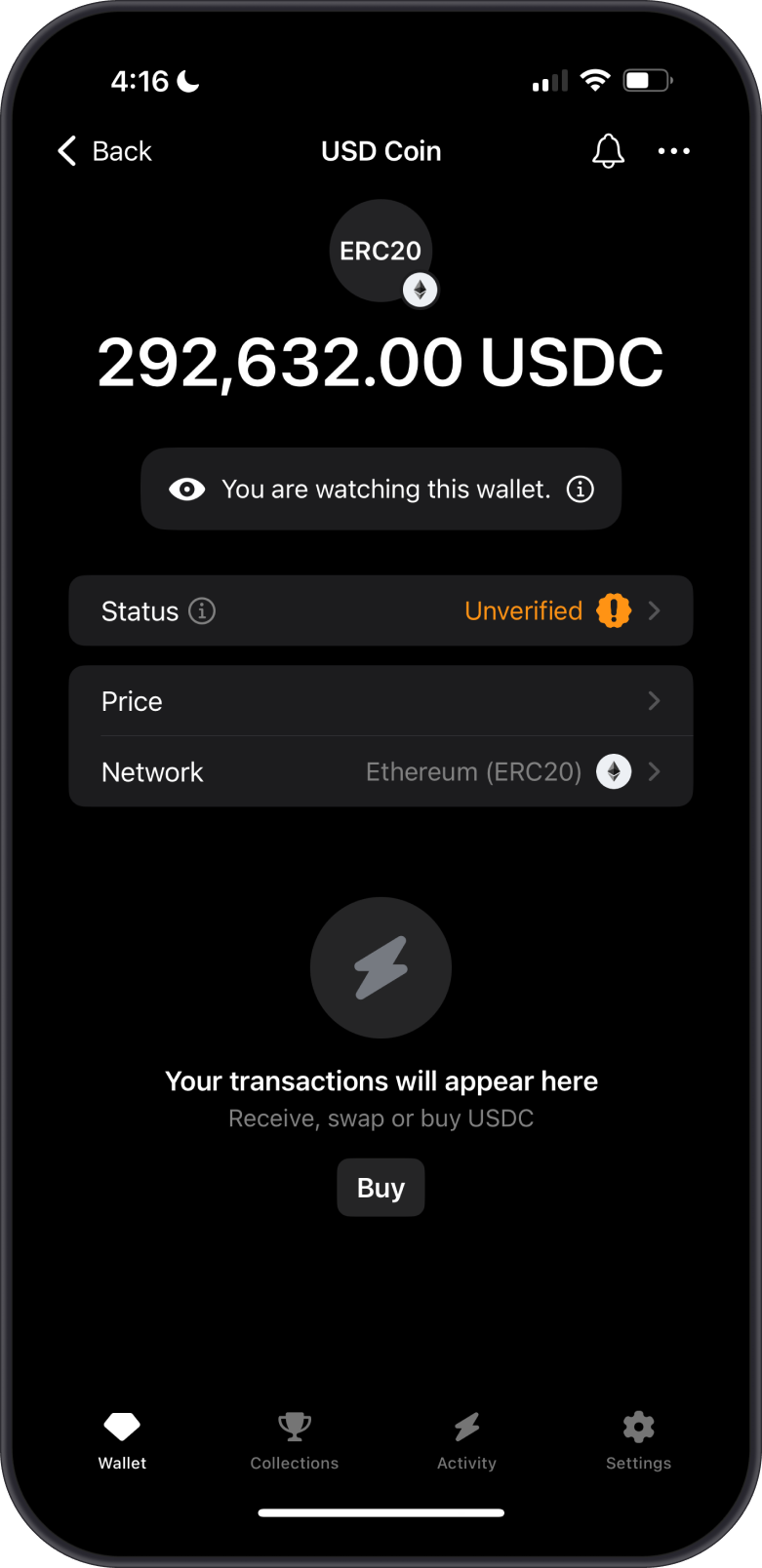
What Are Unverified Tokens?
Unverified tokens are not been vetted by trusted third parties. They may appear in your wallet due to airdrops, transfers, or manual imports. These tokens:
- Lack verification from reputable sources or curated token lists.
- May have limited trading volume, liquidity, or transparency.
- Are not necessarily suspicious but carry higher risk until proven legitimate.
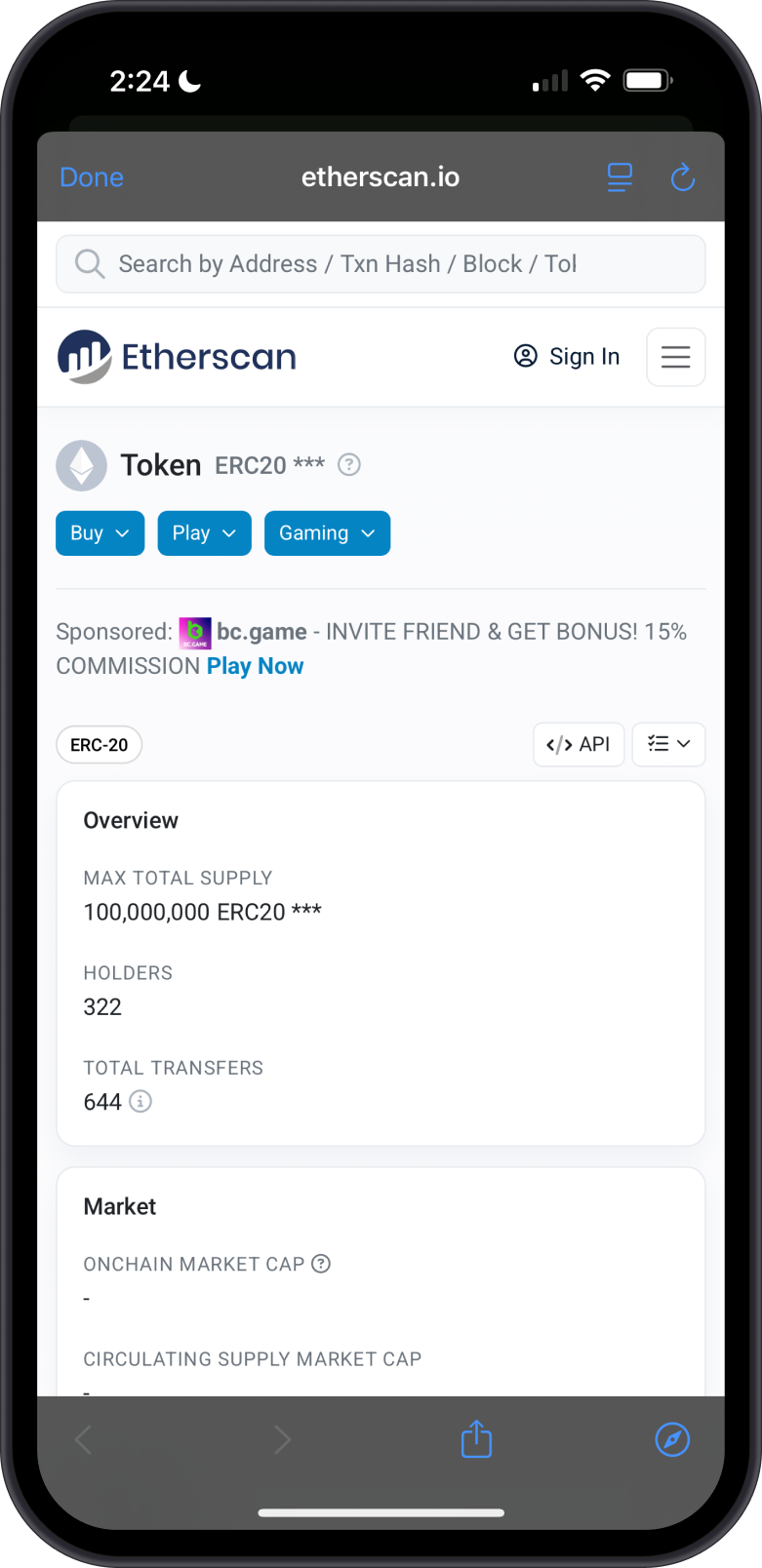
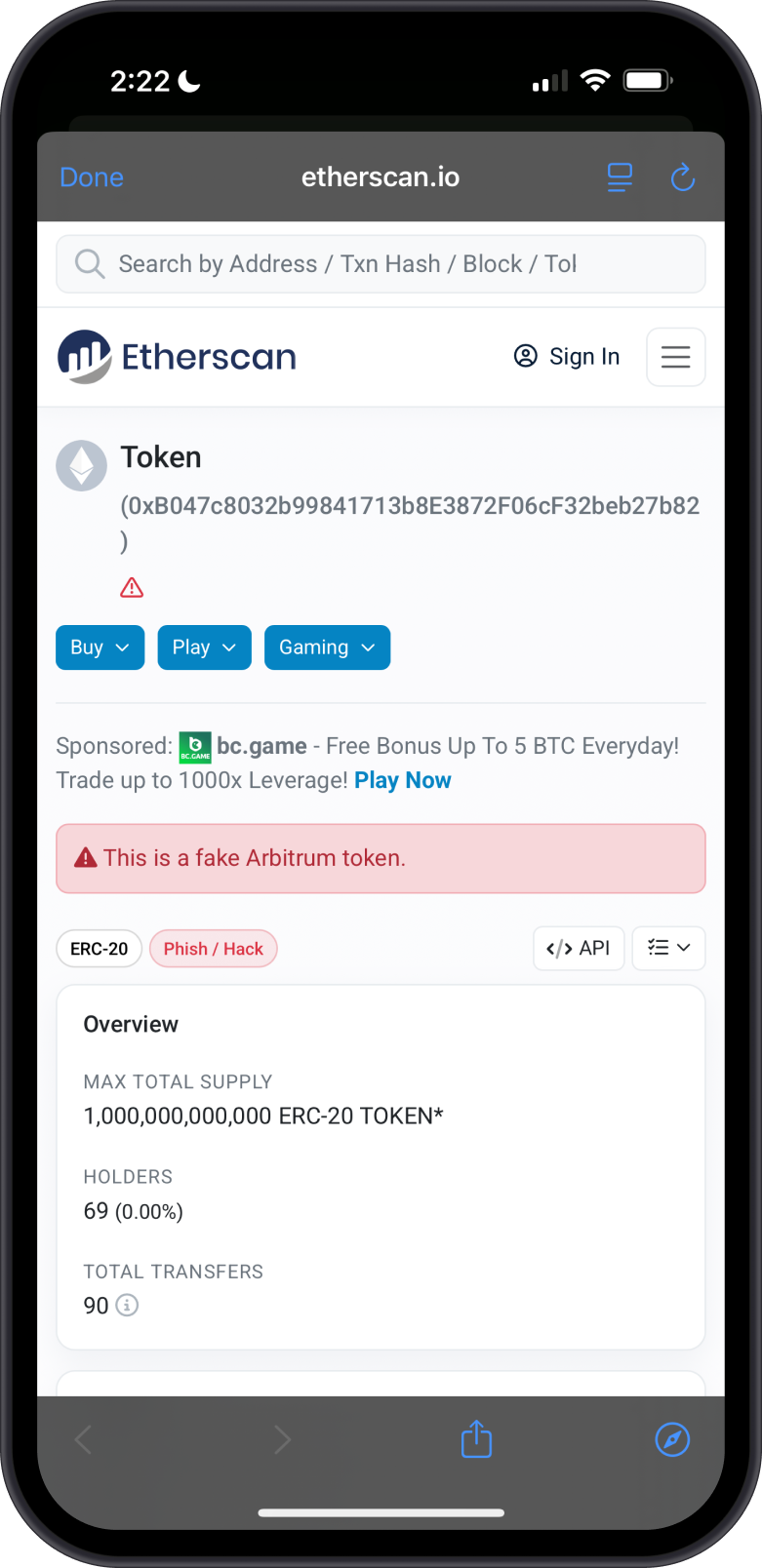
Unverified tokens in Gem Wallet are flagged with a yellow triangle, indicating caution. To investigate further, tap the three-dot menu to view the token on Etherscan, where you may notice it has only a few holders and transactions. In contrast, legitimate tokens typically have a broader distribution across many addresses.
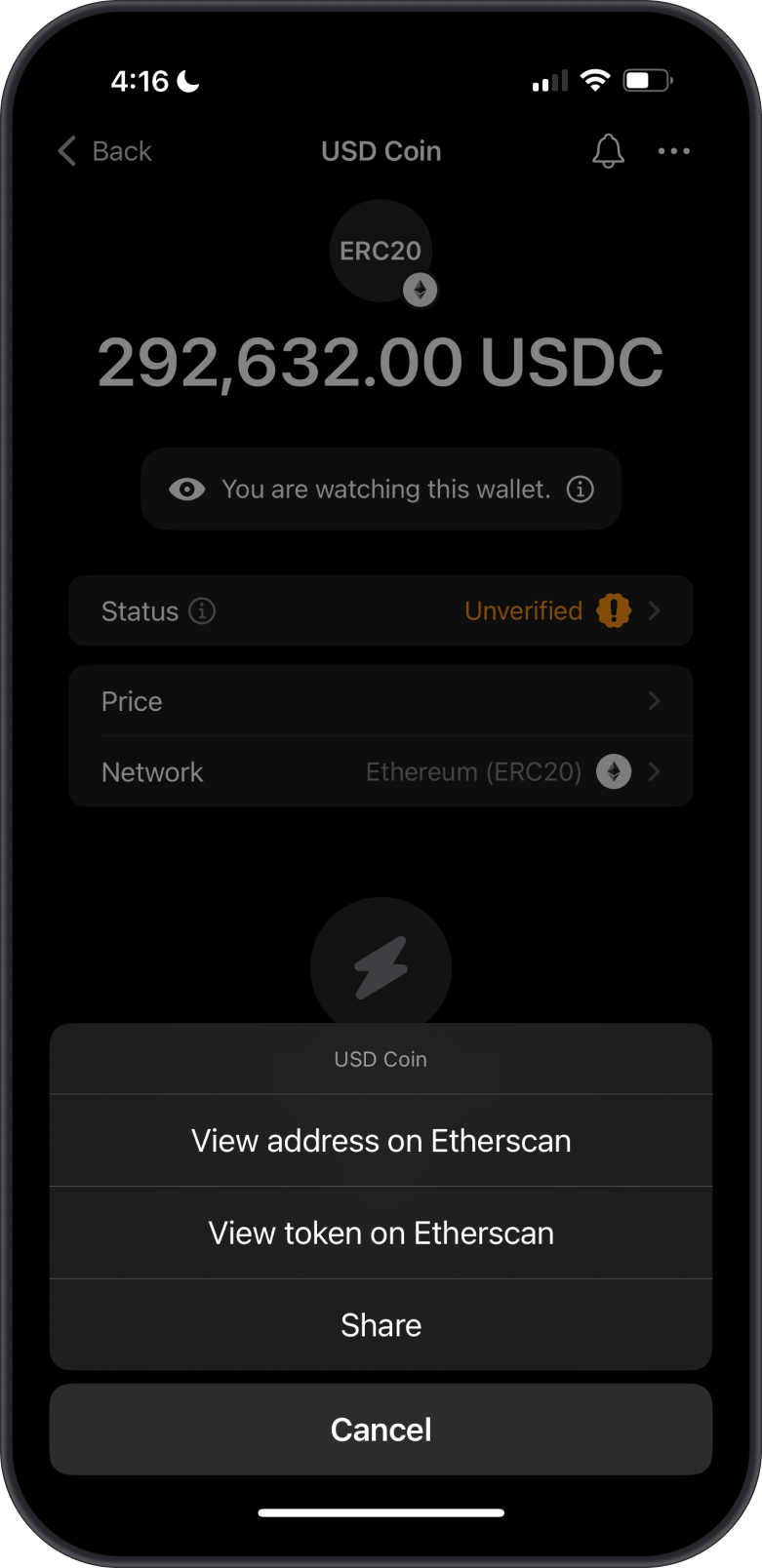
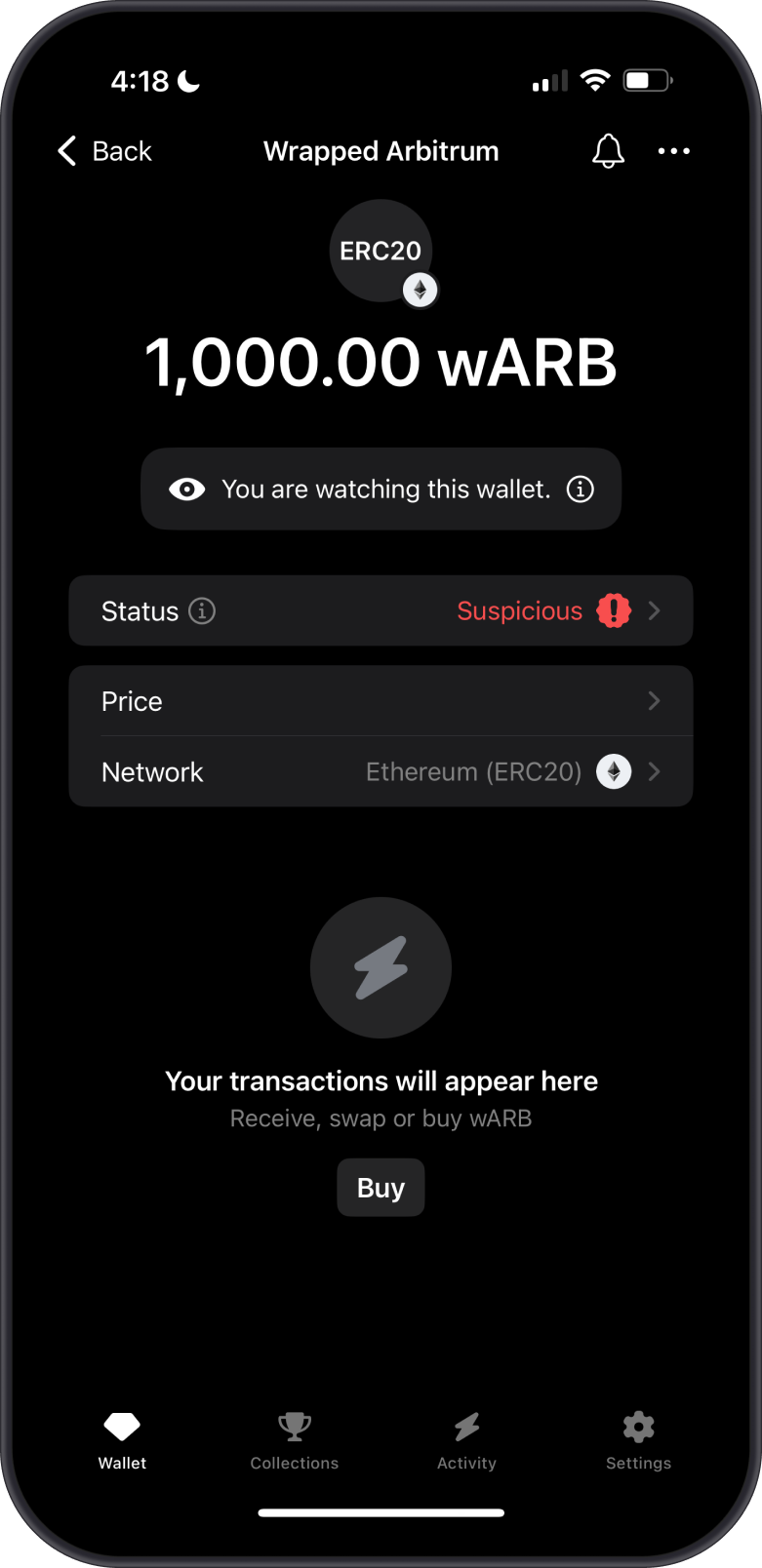
What Are Suspicious Tokens?
Suspicious or spam tokens are identified as potential scams or harmful assets. These tokens:
- Are often sent unsolicited to wallets as part of phishing scams or airdrop fraud.
- May link to suspicious smart contracts that can compromise your wallet if interacted with.
- Are flagged by Gem Wallet’s security checks or community reports as dangerous.
Suspicious tokens in Gem Wallet are flagged with a red exclamation mark, signaling a strong warning against interaction. Third-party sites, such as token scanners or blockchain explorers like Etherscan, often provide additional warnings or flags for these tokens, indicating potential risks like scams or malicious contracts.
How Does Gem Wallet Identify Token Status?
Gem Wallet uses a combination of automated and manual processes to categorize tokens:
- Trusted Lists: Verified tokens are sourced from curated lists like those on CoinGecko, CoinMarketCap, or blockchain-specific registries.
- Security Checks: Suspicious/spam tokens are flagged based on community reports, known scam databases, or suspicious on-chain activity (e.g., low liquidity, abnormal transactions).
- Community Feedback: Gem Wallet may update token statuses based on user reports or new information from trusted sources.
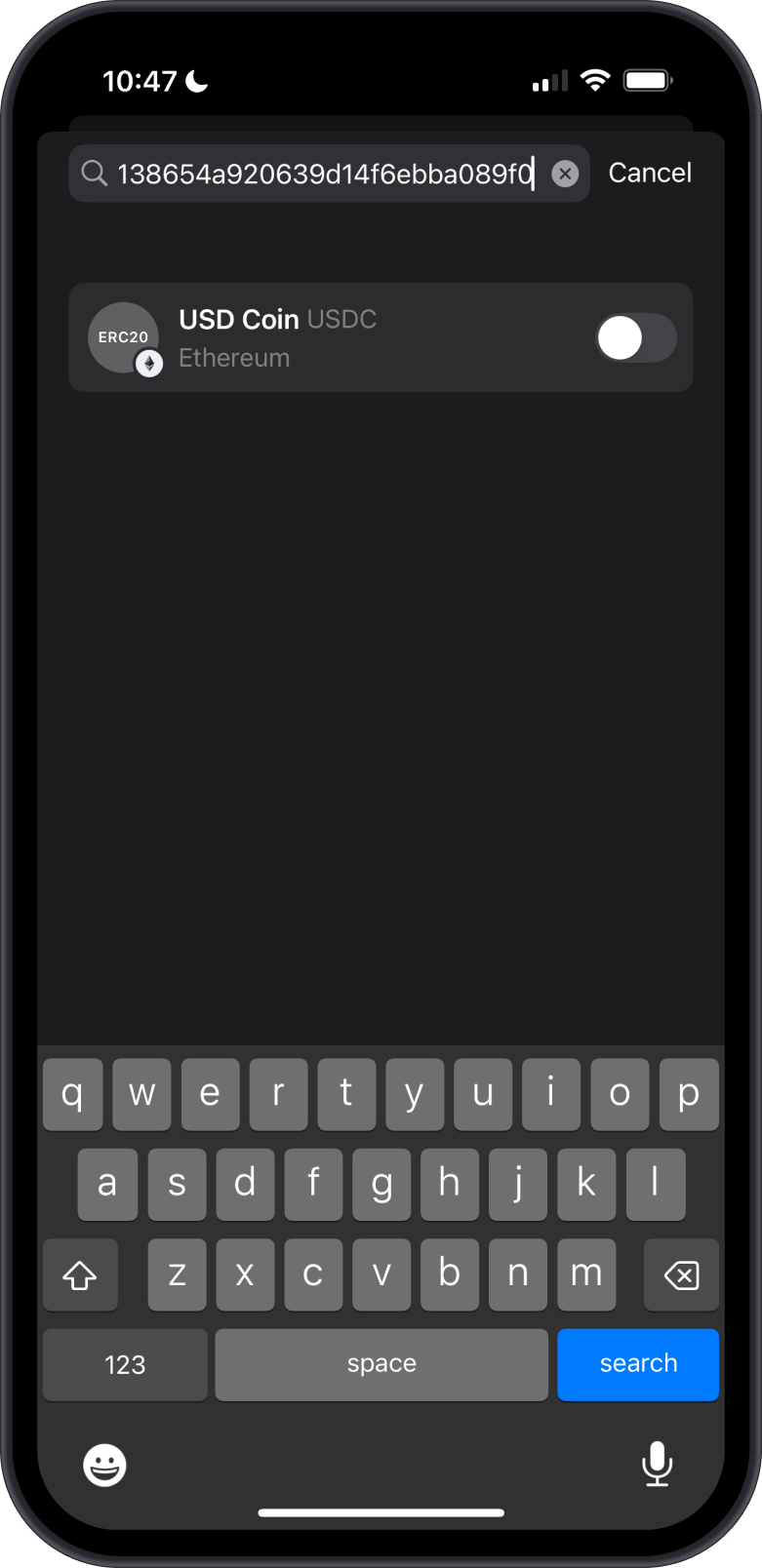
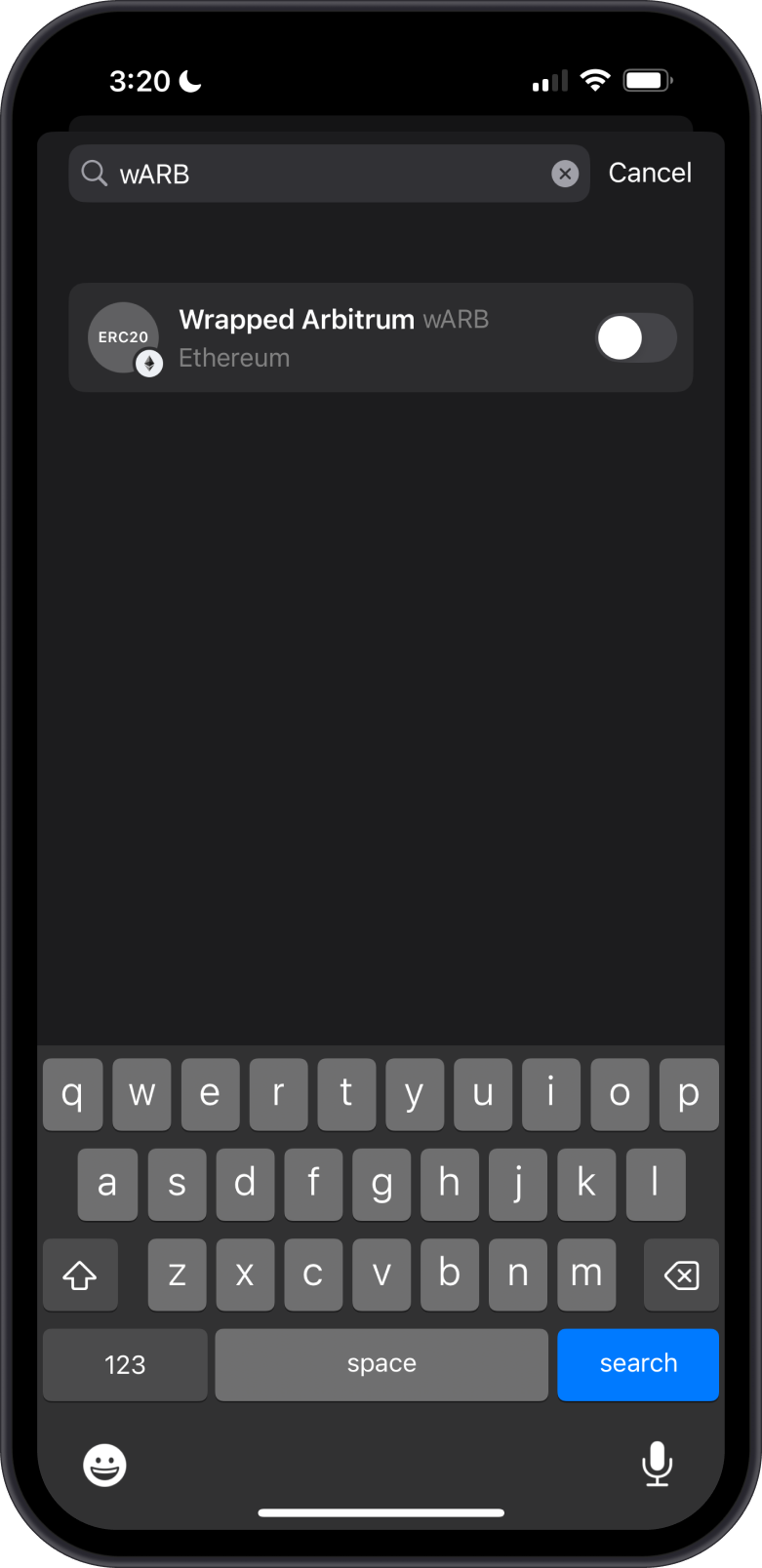
Hide Unverified or Suspicious Tokens on Gem Wallet
To safeguard your wallet from unverified and suspicious tokens, you can hide them in Gem Wallet to prevent them from appearing in your interface, reducing the risk of accidental interaction. Go to the Manage Token List section and then search for the contract address or the ticker and then slide the toggle to the off position.
By hiding suspicious tokens and staying vigilant, you can better protect your wallet from potential threats while keeping your interface clean and secure.
Best Practices for Safe Token Management
- Verify Before Interacting: Check token details on trusted platforms like CoinGecko, CoinMarketCap, or official project websites. Confirm the contract address matches the official one.
- Avoid Unknown Tokens: Do not interact with unverified or suspicious/spam tokens, as they may connect to harmful smart contracts.
- Research Thoroughly: For unverified tokens, check the project’s website, whitepaper, team, and community engagement. Look for red flags like anonymous teams, low liquidity, or suspicious airdrops.
- Secure Your Wallet: Never share your Secret Phrase or private keys. Use Gem Wallet’s biometric login or PIN protection for added security.
- Report Suspicious Tokens: If you suspect a token is suspicious, report it via Gem Wallet’s support channels to help protect the community.